According to the Canadian Anti-Fraud Centre, "Canadians fell victim to fraud, losing more than $96 million." On the other hand, the Association of Certified Fraud Examiners report states that "US businesses lose an average of 5% of their gross revenues to fraud." There is no exception in fraud. Therefore, on-going fraud prevention-related education session is an essential practice for responsible businesses.
Amongst the different types of frauds, spoofing is one of the most common types of attack for small and medium-sized businesses (SMBs).
What is spoofing?
Spoofing is a growing trend amongst scammers and cybercriminals. Especially now with the digital communication demands. Spoofing occurs when the scammer disguises themselves as a trusted source to access sensitive data or information. There are multiple communication channels where spoofing can happen, such as emails, websites, phone calls, or text messages.
Successful attacks can lead to infected devices or computer networks, affecting a business' reputation, revenue, data, and personal information. In most cases, the attacker will provide a dangerous link and/or request an urgent task that involves sending a large amount of money. It is essential to be up-to-date on new trends on various spoofing types as spoofing can be highly detrimental.
What are the different types of email spoofing?
Of different spoofing attacks, email spoofing is the most common type of spoofing that SMBs face.
1. Business executive spoofing
Business executive spoofing, also known as chief executive officer (CEO) fraud, is when the scammer pretends to be a CEO or c-level employee. The primary targets of this scam are employees within the company and most commonly approached through phishing emails. The scammers may use the name of the CEO or another c-level employee with a similar but different email address. In more sophisticated cases, the scammer can disguise their email as identical to the CEO or another c-level employee.
According to the Canadian Anti-Fraud Centre, there are two primary forms of business executive spoofing:
Gift card
The email claims that the boss is working offsite and needs help to buy gift cards for employee rewards or birthday gifts.
Wire transfer
The email directs the employee to urgently transfer a large sum of money to a foreign account through a wire transfer (e.g., more than $100,000).
2. Client spoofing
Client spoofing typically occurs in financial institutions where the scammer claims to be an existing client of an investment broker, financial dealer, or financial controller. The scammer's goal is to trick the employee into thinking that the client needs to make an urgent payment and typically communicate this through email. Similar to CEO spoofing, the scammer will request a large wire transfer to a foreign account.
3. Head office spoofing
Head office spoofing is when the scammer calls a franchise claiming to be from the head office. The scammers will usually target businesses that offer financial products such as gift cards or money transfers. The scammer will report an issue with a financial product asking to activate multiple gift cards and provide them with the gift card numbers. Furthermore, the scammer may ask the employee to conduct a series of money transfers to a foreign account.
4. Payroll spoofing
Payroll Spoofing is when the scammer claims to be an existing employee of the company who needs to change their direct deposit information. The most common form of communication in this trend is through email. The scammer's primary goal is to trick the company into depositing the employee's pay cheque into a fraudulent account. The scammers will typically target the human resources (HR) representatives or financial controllers of a business.
5. Supplier spoofing
Like payroll spoofing, supplier spoofing is when the scammer sends a phishing email to a business and claims to be an existing supplier, wholesaler, or contractor. Supplier spoofing mostly happens in two different ways:
- The scammers trick the company into changing the supplier's payment details. The scammer will claim that they have changed their banking information or request payments deposited into a "new" bank account. Moreover, ask for future payments to be continuously deposited into the "new" bank accounts.
- The scammer will then claim to be the supplier and provide the business with a dangerous fake invoice attachment intended to add malware and gain control of the device.
How to protect your business from spoofing
1. Education
In today's time, educating and creating awareness are essential factors in protecting the business and the employees from fraud. Depending on the industry, semi-annual or even quarterly sessions should be held to educate everyone about fraud and phishing attempts. Additionally, it is helpful to conduct quarterly "phishing email tests," especially if you are in the financial industry. Educating staff goes a long way. If you are having trouble finding a suitable method, there are multiple resources online that offer fraud and phishing training programs:
- Cybersecurity for Small Business by Federal Trade Commission
- Cyber Security for Small Business by Canadian Centre for Cyber Security
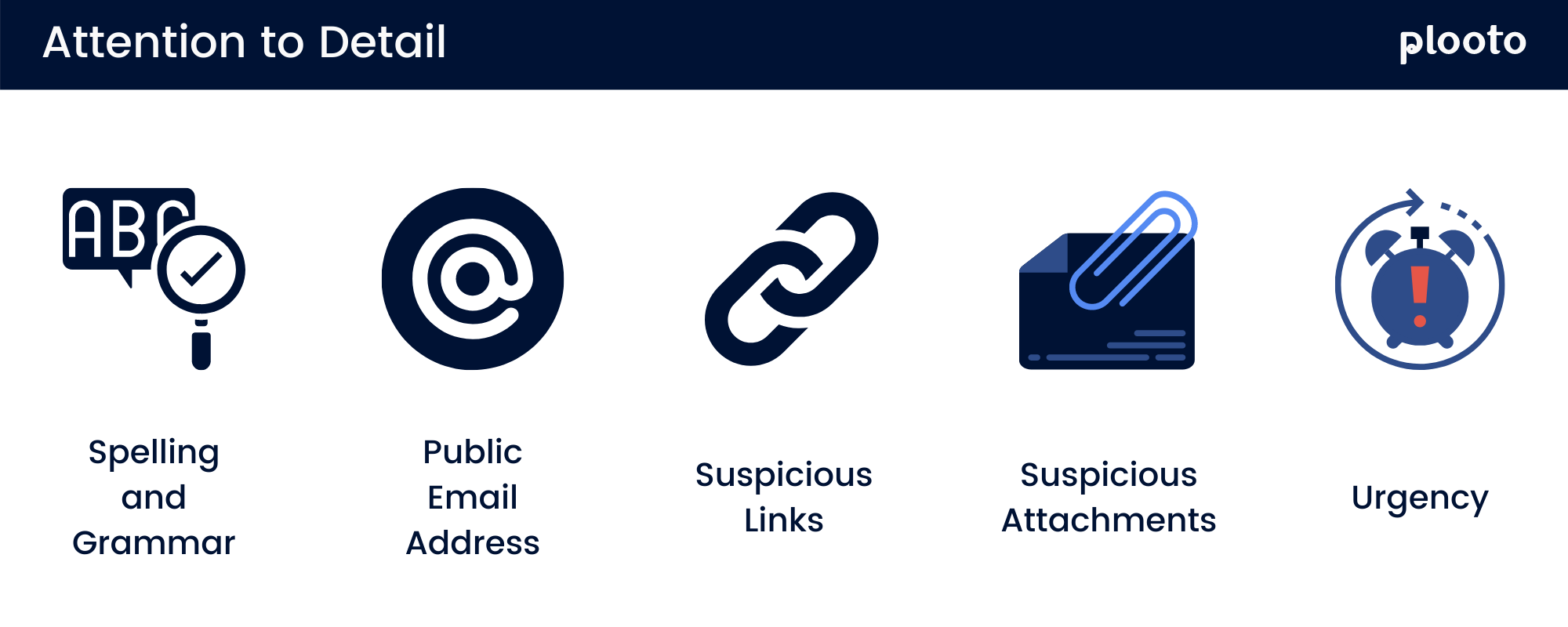
2. Attention to detail
-
Spelling and grammar
Scam messages are most often poorly written or worded. Pay attention to the spellings and grammatical errors in sentences, names, or domains.
-
Public email address
In most cases, scammers use suspicious email addresses that do not belong to a business and typically have a public email address domain (e.g., aol.com or gmail.com). It is essential to look at the email address and NOT the display name of the sender. Individuals need to pay closer attention when viewing the email using a mobile device as the email addresses are always hidden, allowing scammers to leverage the feature to trick most people.
-
Suspicious links
In many cases, the scammers will use a fake link that appears legitimate. Therefore, when a hyperlink is included in an email, it is crucial to hover the link before clicking the link.
-
Suspicious Attachments
Always look for anything suspicious in the email before opening any attachments and never open the attachment unless you are fully confident of what it is. In some cases, the computer may warn you that the file is dangerous or may be harmful.
-
Urgency
The email appears urgent and always involves having to send money. When in doubt, instead of communicating through email, double-check with the sender using an internal communication platform.
3. Approval workflow
Businesses are encouraged to implement a payment solution to avoid spoofing involving payments. Adopting  , a cloud-based payment solution that allows payment approval, will help reduce fraudulent transactions.
, a cloud-based payment solution that allows payment approval, will help reduce fraudulent transactions.
Conclusion
In an ever-growing digital world, security protection from harmful fraud schemes is vital in safeguarding your financial health, sensitive data, and business reputation. Businesses and individuals must be aware and up-to-date with the most common and recent fraud attacks at all times.